Login to Anthos Dashboard and click “view clusters” as shown below
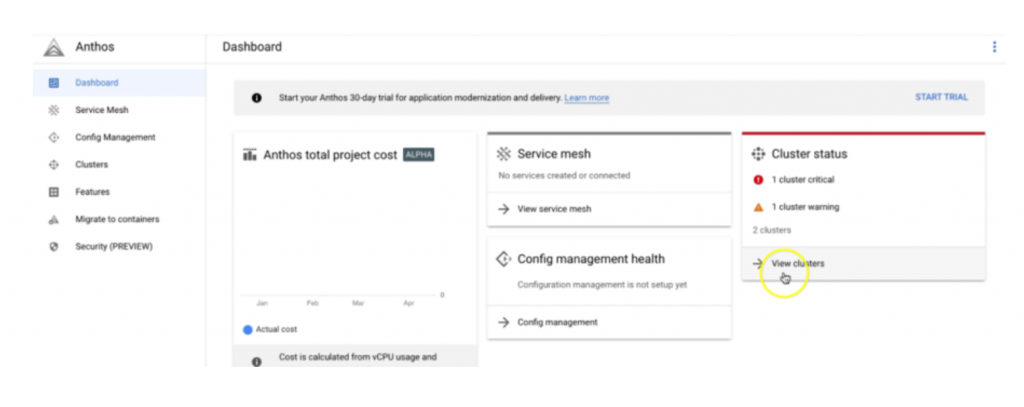
You would see the cluster – “bm-demo-cluster”. This cluster was added to GKE HUB (centralized dashboard ) using GKE connect component. GKE connect agent is installed on the pods in the bm-demo-cluster during installation, which periodically provides the cluster status and listens to required activity feeds from GKE HUB.
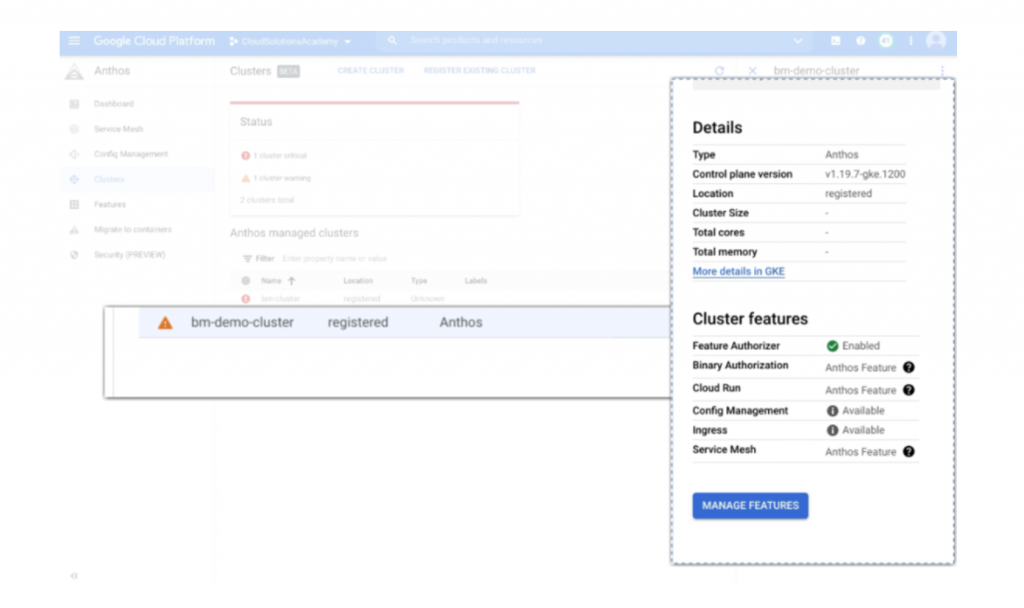
The “bm-demo-cluster “ has a warning sign (as shown above) as you need to login to the cluster. Click on “More detail in “GKE”. You would get a screen with Login option as shown below.

Click on Login in “bm-demo-cluster” and it shows 4 options to authenticate the cluster. We would use token to authenticate the cluster and view the cluster details.
To get the access token, we would first need to create a Kubernetes service account (KSA) with the appropriate roles to manage cluster details. We would create cloud-console-reader for view cluster access and cluster-admin role to allow any installation from Google Marketplace in future.
First export the kube configuration file.
export KUBECONFIG=~/bmctl-workspace/bm-demo-cluster/bm-demo-cluster-kubeconfig
Then execute the following commands in a sequence to create the KSA with appropriate roles
> KSA_NAME=ks-bm
> kubectl create serviceaccount ${KSA_NAME}
> kubectl create clusterrolebinding bm-cl-rb \
–clusterrole view –serviceaccount default:${KSA_NAME}
> kubectl create clusterrolebinding cc-reader-bd \
–clusterrole cloud-console-reader –serviceaccount default:${KSA_NAME}
> kubectl create clusterrolebinding kb-cl-rb \
–clusterrole cluster-admin –serviceaccount default:ks-bm
Once the roles are created, get the bearer token for the KSA, using the following command
> SECRET_NAME=$(kubectl get serviceaccount ks-bm -o jsonpath='{$.secrets[0].name}’)
> kubectl get secret ${SECRET_NAME} -o jsonpath='{$.data.token}’ | base64 –decode
Copy the output from kubectl and paste it in token field on the cluster Login option.
You should see the green icon next to the cluster and should be able to view the cluster details as shown in figure below.
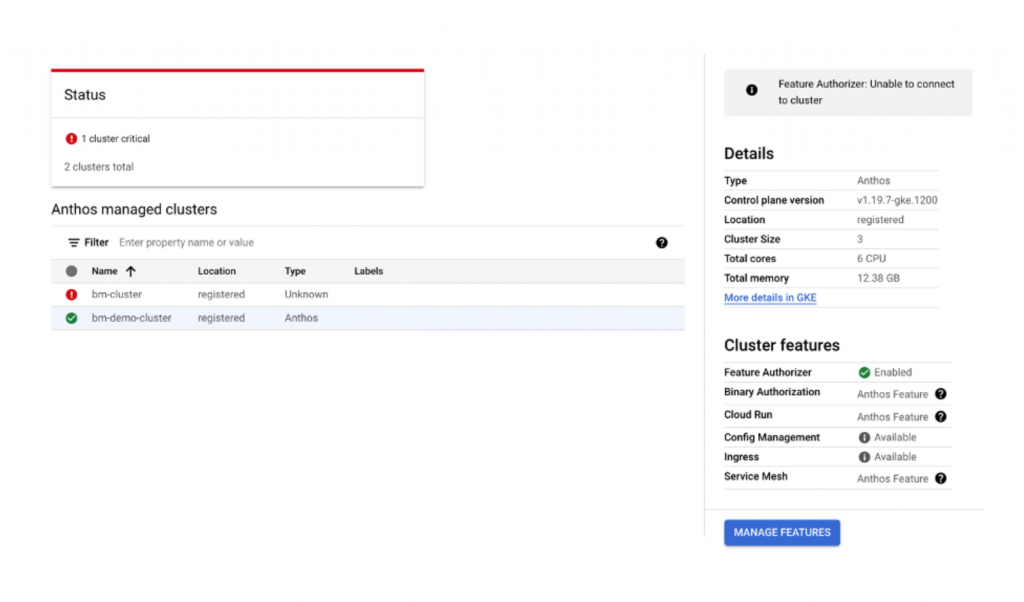
Click on More details in GKE and you can view the bm-demo-cluster details as shown below.
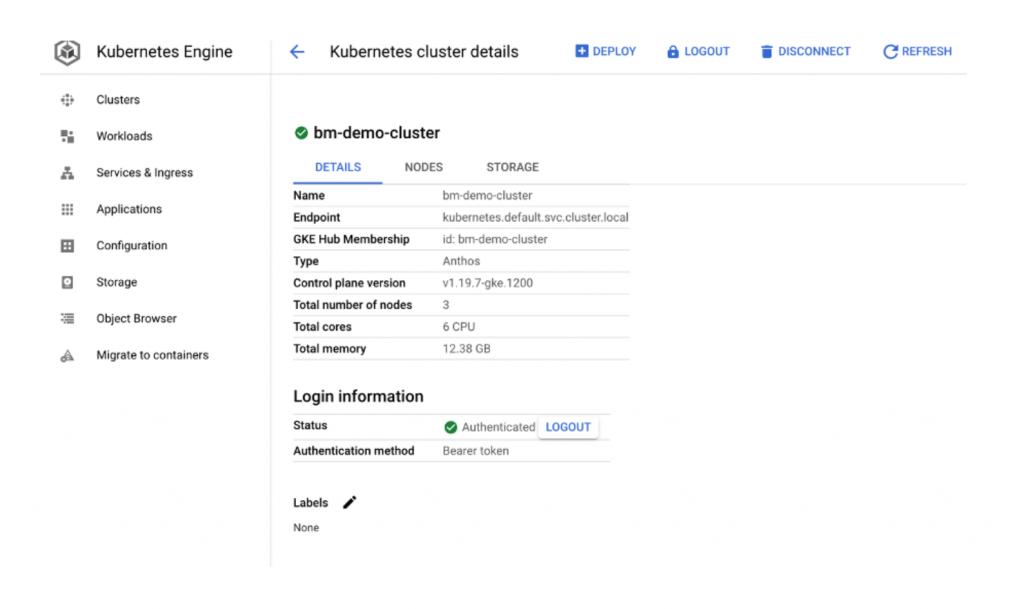
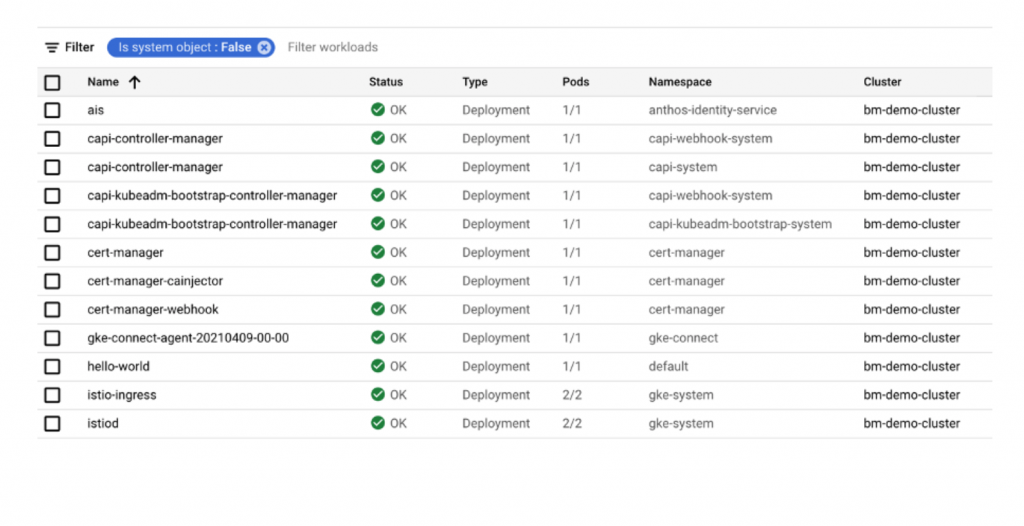
If you click on workloads, you can see all the workloads deployed on the cluster and status should be in green.
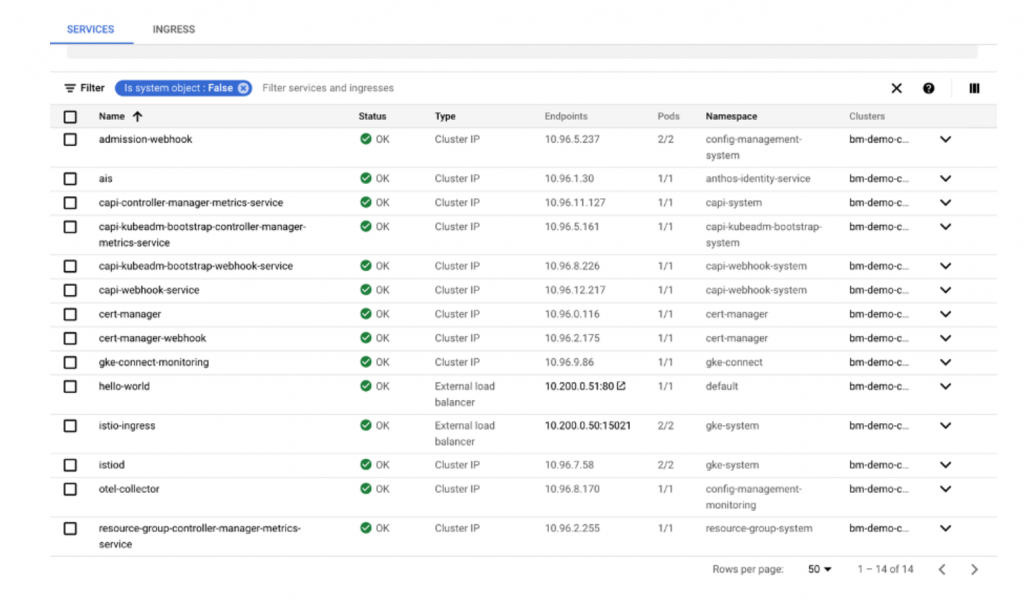
If you click on Service & Ingress, you can see all the services deployed on the cluster and status should be green.
Next we would deploy a sample hello world application to the cluster.