Introduction
Anthos allows you to attach any non-GKE Kubernetes cluster. In this article, I will demonstrate how to attach an existing AWS EKS cluster and make it part of Anthos ecosystem. Once the cluster is attached, you can view and manage it from the Anthos dashboard in the Google Cloud Console. You can also enable features like Anthos Config Management (ACM) to your AWS EKS cluster. The AWS EKS cluster will show up as an external cluster alongside other GKE clusters in the Anthos dashboard.
To attach the AWS EKS cluster, make sure you have the following prerequisites in place:
- AWS EKS cluster with Kubernetes version 1.19, 1.20 or 1.21
- A Google Cloud project with billing enabled
- Anthos API enabled
You will perform the following steps to attach the AWS EKS cluster
- Enable relevant APIs
- Creating Service Account
- Registering the Cluster
- Login into the Registered AWS Cluster
Enable APIs
As a first step, you will enable relevant APIs that will allow you to connect and register your cluster with the hub a.k.a project fleet that will make your cluster part of Anthos ecosystem.
The following commands enables the necessary APIs:
gcloud services enable \ --project=[PROJECT_ID] \ container.googleapis.com \ gkeconnect.googleapis.com \ gkehub.googleapis.com \ cloudresourcemanager.googleapis.com \ iam.googleapis.com
Creating Service Account
As a second step, you will create a service account that will be used by AWS EKS cluster to authenticate against Anthos.
gcloud iam service-accounts create gke-anthos --project=${PROJECT_ID}
gcloud projects add-iam-policy-binding ${PROJECT_ID} \
--member="serviceAccount:gke-anthos@${PROJECT_ID}.iam.gserviceaccount.com" \
--role="roles/owner"
gcloud iam service-accounts keys create gke-anthos-key.json \
--iam-account=gke-anthos@${PROJECT_ID}.iam.gserviceaccount.com \
--project=${PROJECT_ID}
The above command creates a service account named gke-anthos and is assigned the owner role that grants full admin access to the said account. For our use case here, we are simplifying the access privilege by granting the owner permission. But in an ideal world, granting owner role is not recommended and the principle of least privilege should be followed when granting permissions to users or service accounts.
The last command will create and download the JSON key for the said service account. You will use this JSON key while registering the AWS EKS cluster. The JSON key will be used to authenticate the AWS EKS cluster with Anthos.
Registering the Cluster
You will now register the AWS EKS cluster with the project fleet that will allow you to view and manage the cluster from the Anthos console dashboard.
gcloud container hub memberships register aws \ --context=rn:aws:eks:ap-south-1:798531306129:cluster/aws-cluster \ --kubeconfig=~/.kube/config \ --service-account-key-file=gke-anthos-key.json
The above command registers the AWS EKS cluster and creates a membership named aws. The command expects kube config and the context name of the AWS cluster. If you do not create the context for the AWS cluster then by default the context is the cluster’s Amazon Resource Name (ARN). Upon registration, it will install the Connect Agent on the cluster that will enable you to view and manage your cluster from the Anthos dashboard. The Connect Agent pod will be part of the gke-connect namespace. The Connect Agent will authenticate to Google using the earlier generated service account JSON key. Registering a cluster indicates that the cluster is now in the realm of Anthos ecosystem.
You can view the registered clusters by giving the following command:
gcloud container hub memberships list Output: NAME EXTERNAL_ID anthos 158999b6-5e01-4f55-9314-148aac98345d aws-cluster 1245479d-7886-4cf2-91c3-0363fc114910
The view from the console looks like the following:
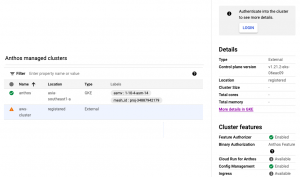
As you can see, the attached AWS cluster is tagged as External which means it is a non-GKE cluster. You will also see an already existing GKE cluster. If you select the AWS cluster and observe the right side panel, you will see it still does not show the memory and CPU values of the cluster. So at this point Anthos does not have the visibility into the AWS EKS cluster. To get the cluster visibility, you will have to login into the cluster.
Login into the Registered AWS Cluster
In order for the Anthos to gain visibility into AWS EKS cluster, you must login into the registered AWS cluster using Kubernetes based secret token that has permission to read cluster nodes. As a first step, create a Kubernetes ClusterRole resource that will have all the permissions to read the cluster nodes.
apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: cluster-node-reader rules: - apiGroups: [""] resources: ["nodes"] verbs: ["get", "list", "watch"]
Connect to your AWS EKS cluster and apply the above YAML. It will create a ClusterRole resource by the name cluster-node-reader. You will now bind this role to the service account by creating ClusterRoleBinding resource.
Let’s first create a Kubernetes service account.
kubectl create serviceaccount anthos
The above command will create the service account by the name anthos. This will also create the secret token of the anthos service account. You can view the secrets by running the following command:
kubectl get secrets Output: NAME TYPE DATA AGE anthos-token-bxktd kubernetes.io/service-account-token 3 8m17s default-token-2nxvq kubernetes.io/service-account-token 3 3d6h
Now you will bind the anthos service account with the earlier create cluster role cluster-node-reader.
kubectl create clusterrolebinding anthos-cluster-node-reader-binding --clusterrole cluster-node-reader --serviceaccount default:anthos
The above command will make sure that the anthos service account is able to view and read the cluster nodes. Now you grab the secret token of this service account and provide this to Anthos as part of login process.
kubectl get secret anthos-token-bxktd -o jsonpath='{$.data.token}' | base64 -D
Output:
xxxhbGciOiJSUzI1NiIsImtpZCI6IjVYbTJjTnA4Y0M1bVZ2ZzV2TDdfZ0lkMXFEOWtIWFh1THotdUpUVHJObFkifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJkZWZhdWx0Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6ImFudGhvcy10b2tlbi1ieGt0ZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhbnRob3MiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiIwMmNlZDBiNS04NjI1LTQ3NzAtOTZjNi1mMjZjZDk1YTE3NzIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6ZGVmYXVsdDphbnRob3MifQ.CsYhcHbmVUHPzsbr8skeEh9eVWecHnZGoY1c8B52jjlpDi6_HBcqaxiq-hjdVMGcdkJDPBqKZVhdWMLqG0vb2OuLBLeR4ktD_pahrYV9ZkL2CVCrKE4-HD6m2ljX8U_XfJ_ENAficziMs1fgJ4Em70YoGO2xvmauBRy7WehZfhmW6WGQqXM8dNkBmNwCnhoxxzxF3QxQb3RH_ltIkI8xUOpL3Eg7dSCyVyuFRixjtU2Vonnz-FR5GwThB2HvAyZ0Tdw7tufE19_Y68dL4Uspxv2V5nflS95tpvVSxF5RNVqyZby6QRFqtj0Bs4BMk0KpHUTg_bmLHuc9ARHklXMLzzz
You already know the name of the secret from the earlier command. You get the data of that secret which is encoded as base64 and decode it. It will print the decoded data (see the above output).
You will now copy the above decoded secret data and paste it while performing login into the registered AWS cluster from the Anthos cluster dashboard.
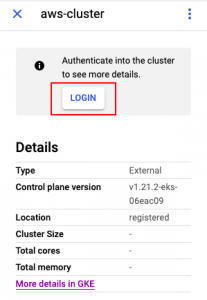
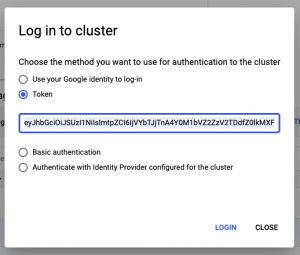
Click on the LOGIN button and chose Token as an authentication method. Paste the decoded secret data and perform login. You will now see the AWS EKS cluster resource details like memory and CPU.
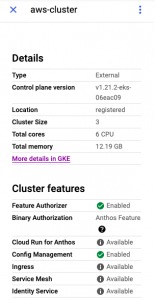
Anthos now has visibility into the AWS EKS cluster and displays the cluster size, total CPU cores and memory.
As you can see, it is so easy to make existing non-GKE cluster part of Anthos ecosystem. Going ahead you could use features like ACM to automate the deployment in a multi cluster environment.